- Crypto payments provider CoinsPaid was hacked for $37 million last month.
- The hack was most likely carried out by the North Korea-linked Lazarus Group, according to a report shared with DL News.
- Hackers tricked a CoinsPaid employee into thinking they were being interviewed for a lucrative job and downloading malicious software.
CoinsPaid, a crypto payments provider, has unveiled the intricate details of the $37 million heist it suffered on July 22.
The sophisticated attack was orchestrated by North Korea’s notorious Lazarus Group and involved a six-month-long campaign of relentless social engineering, culminating in an employee being manipulated via a deceptive job offer, according to details shared with DL News.
The breakdown of the $37 million hack provides a detailed look at the tactics of North Korean hackers, who have become the bane of the crypto industry. Crypto heists fund the nation’s rogue nuclear weapons programme, according to experts.
NOW READ: North Korea accelerates nuclear missile programme with ‘treasure sword’ — $1.7bn from crypto heists
Lazarus Group tends to use similar hacking techniques, blockchains, exchanges and mixers, as well as some of the very same crypto wallet addresses, according to CoinsPaid and crypto security firm Match Systems. That led them to conclude the notorious hacking outfit tied to the North Korean government was responsible for the hack.
Lazarus’ rap sheet includes some of the largest hacks in crypto. Last year, the group stole more than $620 million from the blockchain-based video game Axie Infinity. That hack was also pulled off after hackers tricked a company engineer into applying for a fake job, according to reporting from The Block.
Other major hacks include the $100 million hack of the Harmony blockchain last year and the $115 million hack of Atomic Wallet in June.
NOW READ: Atomic Wallet faces $100m lawsuit following North Korean hack
In total, Lazarus Group and other hackers linked to North Korea have stolen more than $3 billion in cryptocurrency, according to estimates from Chainalysis.
Ethereum security researchers Taylor Monahan and pseudonymous ZachXBT found that more than $8 million in crypto from the CoinsPaid, Atomic Wallet and Harmony hacks were batched and moved from Ethereum, to Avalanche, and then to Bitcoin in recent days.
A few nights back, @zachxbt and I stumbled on a crazy direct link btwn funds stolen from Coinspaid/Alphapo <> Atomic Wallet <> Harmony.
— Tay 💖 (@tayvano_) August 3, 2023
Last night, ~$8.5m of the funds from Coinspaid/Alphapo (w/ some leftovers from Atomic Wallet) went flying across 300+ addies on 3 chains.
😳 https://t.co/onn6v75JxW pic.twitter.com/10DNH11F6L
“I’m going to be completely honest and say that watching Lazarus gratuitously run circles around the blockchains like this is pretty gross,” Monahan said.
“In the last 2 months, DPRK has stolen $290m+ from thousands of hard-working people who build crypto products, use crypto products, and try to contribute to this ecosystem.”
How CoinsPaid was hacked by Lazarus Group
Lazarus spent a staggering six months meticulously tracking and studying CoinsPaid’s systems, attempting various forms of attack ranging from social engineering to technical attacks like Distributed Denial-of-Service and brute forcing — submitting many passwords with the hope of eventually guessing correctly.
In March, hackers began attacking CoinsPaid.
“The spam and phishing activities against our team members were constant and highly aggressive,” said the company’s post-mortem report shared with DL News.
In March, engineers at CoinsPaid were sent a list of questions regarding technical infrastructure from a supposed “Ukrainian crypto processing startup.” In June and July, engineers received fake job offers and bribes. On July 7, a “massive attack” involving 150,000 IP addresses hit CoinsPaid infrastructure and applications.
Although the series of attacks were unsuccessful, information gained during the campaign helped the hackers pull off the successful, $37 million heist on July 22.
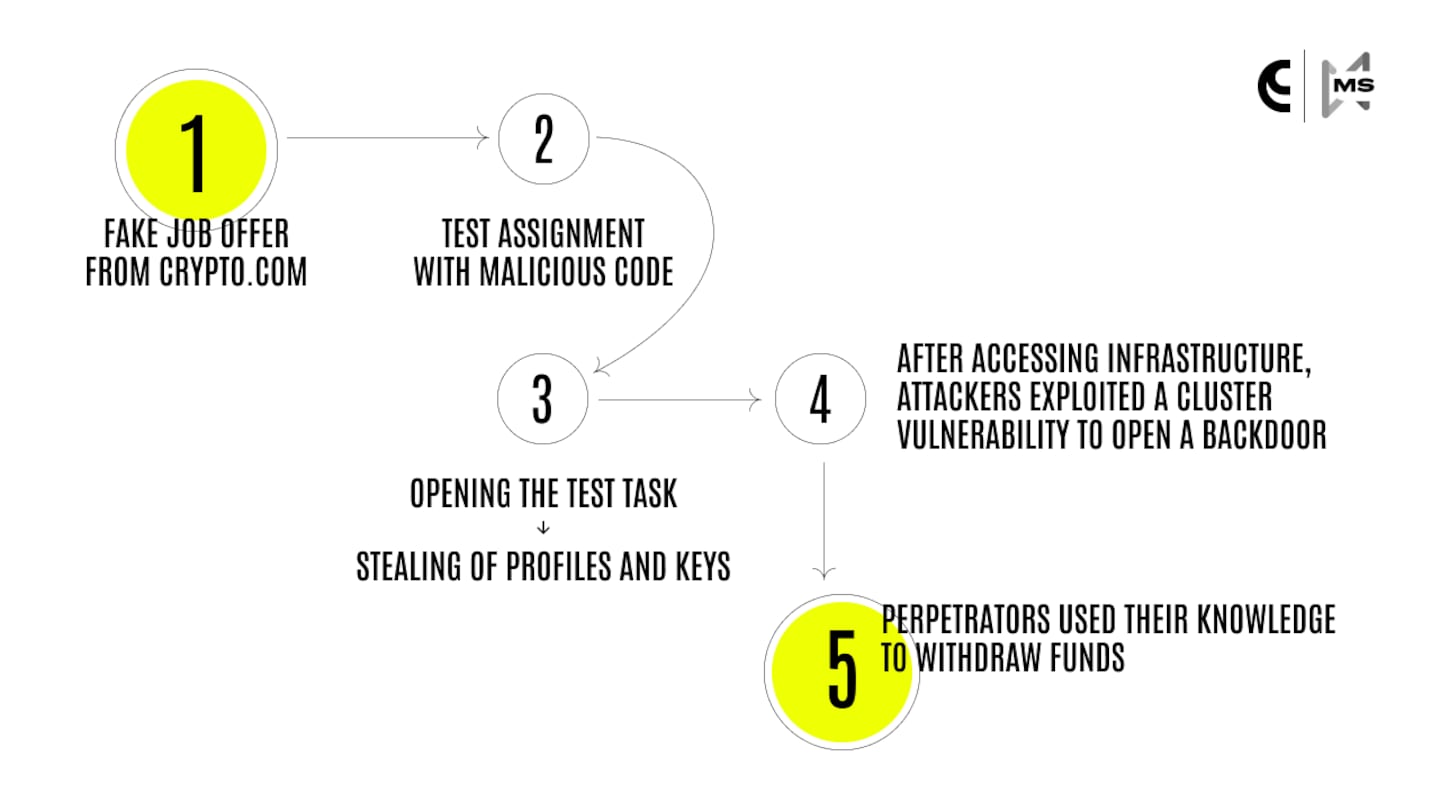
That day, an employee at the company, under the impression they were being interviewed for a lucrative job with centralised crypto exchange Crypto.com, downloaded malicious software as part of a supposed technical test.
“Although you may think that such an attempt to install malicious software on the employee’s computer is obvious, the hackers had spent 6 months learning all possible details about CoinsPaid, our team members, our company’s structure, and so on,” CoinsPaid said in its report.
“Such top-tier hacking groups as Lazarus are able to create a completely believable story to take advantage of potential targets.”
When the employee downloaded the malicious code, it gave hackers access to CoinsPaid’s system, where they were then able to exploit a software vulnerability to successfully fake authorised requests to withdraw funds from CoinsPaid hot wallets.
CoinsPaid said the hackers could not breach the hot wallets themselves and “acquire private keys to access funds directly.”
The hackers then withdrew most of the money to crypto bridge SwftSwap, with some also going to decentralised exchange SunSwap on the Tron blockchain and a so-called swapper, SimpleSwap. Hackers also sent money to mixers that obscure the movement of crypto such as Sinbad, in order to avoid know-your-customer and anti-money laundering requirements, according to CoinsPaid.
NOW READ: How hackers turn stolen crypto into cash
The fake job offer wasn’t an isolated incident. The attackers repeatedly employed advanced social engineering techniques during their six-month campaign, targeting CoinsPaid employees with enticing job offers at companies like LinkedIn, offering salaries ranging from $16,000 to $24,000 a month.
The hackers aimed to manipulate candidates into installing JumpCloud Agent, a directory platform reportedly compromised by Lazarus in July 2023.
CoinsPaid is preparing a roundtable discussion on North Korean hacking, and said it had learned a couple lessons from the incident.
Those include the necessity of training employees to recognise social engineering tactics, including fake job offers, and understanding that small, unsuccessful hack attempts might simply be preparation for a much larger operation.
The Estonia-based company previously said the hack only affected its revenue, and that no customer funds were lost.
Update, August 7: This story was corrected to note that 150,000 IP addresses were involved in an attempted hack on CoinsPaid on July 7.